On September 17th, the news is that today, as technology continues to innovateAIThe pace of empowerment is also accelerating. In the area of cyber security, the use of artificial intelligence also allows for responseCyber attacksMore efficient。
According to op-ed reports, today, the National Cyber Security Awareness Week Artificial Intelligence Security Governance Sub-Forum was held in Kunming, Yunnan, where guests explored in depth the issues of artificial intelligence risk challenges, governance initiatives, application security and algorithm security。
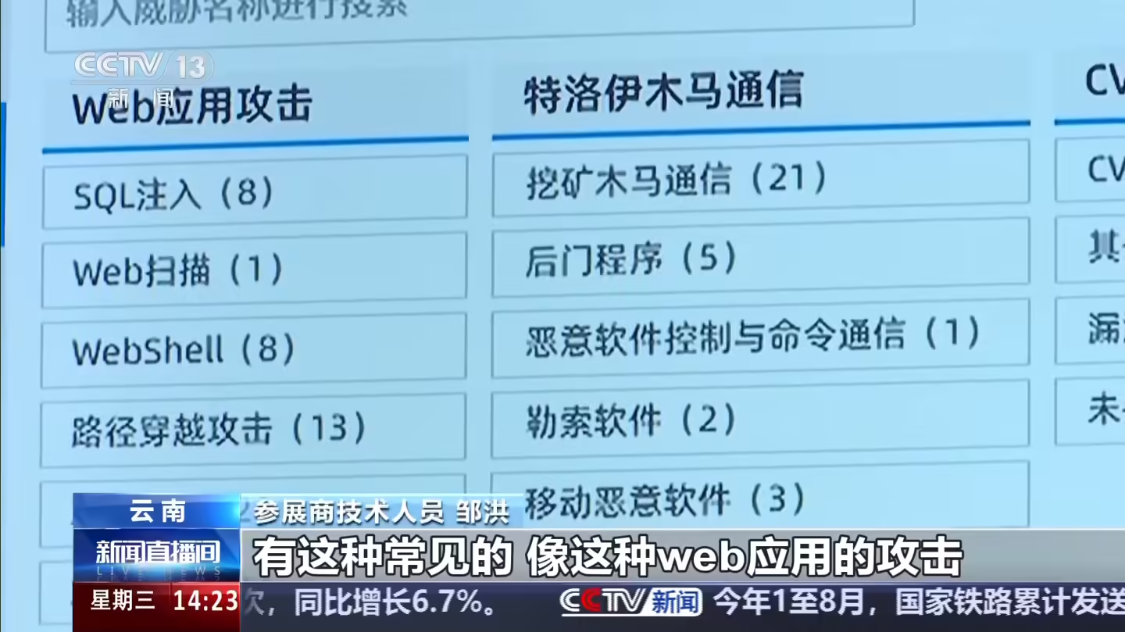
The exhibitor ' s technicians Zouhong described the many types of cyberattacks to be faced by large enterprises, such as the most common Web-based threats of diverse networks such as attacks and encrypted carp communications。
According to technicians, in the past the response to cyberattacks was mainly manual and time-consuming. Introducing AI Thereafter, different models can be built to screen the police levels of cyberattacks for more efficient response。
ZOUHONG STATES THAT WE HAVE TAKEN A THREE-TIER (SCREENING) APPROACH TO THIS ALARM THROUGH A STRUCTURE THAT BLENDS THIS LARGE AND SMALL MODEL. WE CAN FIND A REAL THREAT TO CYBERATTACKS, A NOISE REDUCTION ABOVE 98%。
FOR THE REMAINING PARTS REQUIRING MANUAL RESEARCH, THE AI LARGE MODEL CAN ALSO ASSIST IN ANALYSING, TRACE THE SOURCE OF THE ATTACKER AND FURTHER ACCELERATE THE PROCESSING OF CYBERATTACKS. AS FAR AS AI IS AWARE, AFTER THE TECHNICIANS HAVE OBTAINED INFORMATION ABOUT THESE ATTACKS, THEY CAN THEN BE HANDED OVER TO THE PUBLIC SECURITY ORGANS AND THE RELEVANT STATE AUTHORITIES FOR FURTHER DISPOSAL。
IN THE CASE OF CYBERATTACKS CARRIED OUT BY A NUMBER OF OUTLAWS USING AI LARGE MODELS, TECHNICIANS ALSO INDICATED THAT THERE WAS A NEED FOR AN AI RESPONSE TO AI TO PROVIDE CYBERSECURITY PROTECTION。
ZOUHONG INDICATES THAT, BECAUSE A LARGE MODEL INITIATES CYBERATTACKS, THERE WILL BE FEATURES, SUCH AS A HIGHER FREQUENCY OF ATTACKS AND A RELATIVELY FIXED PATTERN OF ATTACKS, WE WILL LEARN ABOUT ITS ATTACK BEHAVIOUR AND PATTERN OF ATTACK BY WAY OF AI, AND, AFTER MODELING, WE WILL MOBILIZE OUR SECURITY EQUIPMENT TO AUTOMATE THE INTERCEPTION OF IT BY MEANS OF AI。